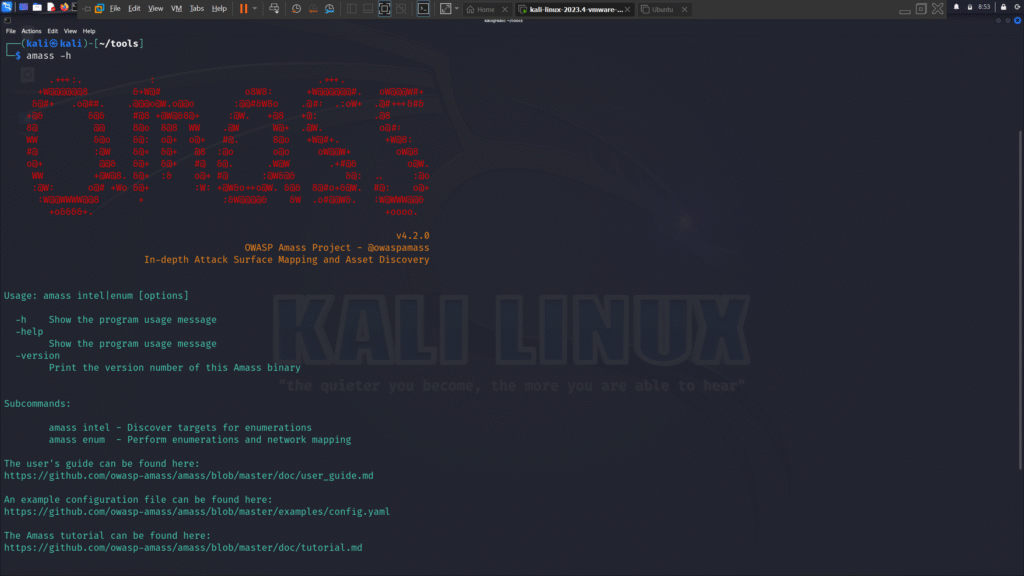
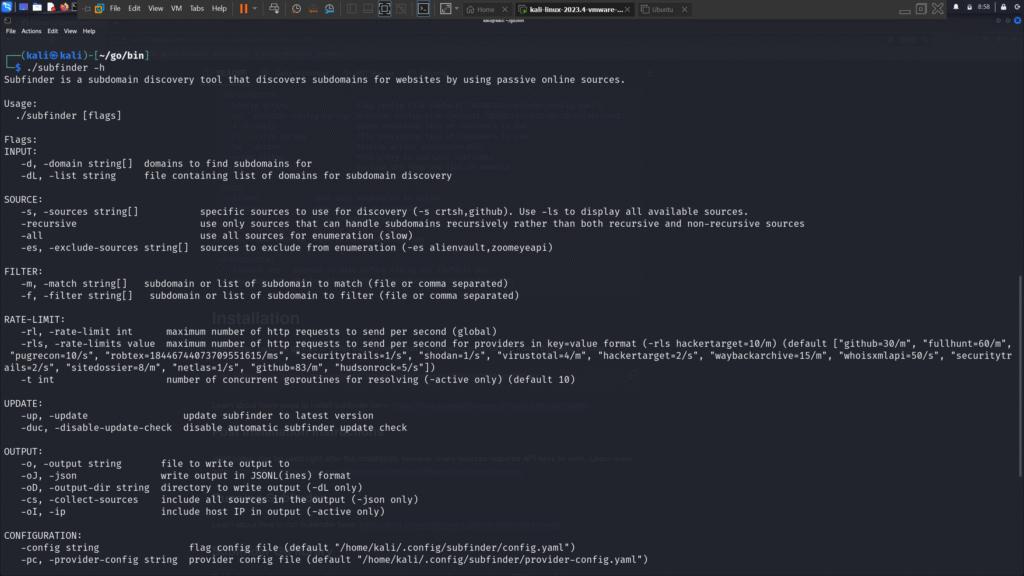
In an increasingly digital world, securing applications, systems, and user data has become more critical than ever. Organizations now realize that no security system is infallible, and as a result, many have turned to a collaborative approach—inviting ethical hackers from around the world to help identify vulnerabilities before malicious attackers do. This has given rise to the practice of Bug Bounty Hunting.
Bug bounty programs offer financial rewards, recognition, and community credibility to security researchers who identify and report vulnerabilities responsibly. If you’re curious about entering the world of cybersecurity, bug bounty hunting is a thrilling and rewarding starting point. In this guide, we’ll cover everything you need to know to get started—from the skills you’ll need to the platforms that host these programs.
- What Is Bug Bounty Hunting?
- Why Become a Bug Bounty Hunter?
- What Skills Do You Need to Start?
- Setting Up Your Home Lab
- Tools of the Trade
- Reconnaissance: Your First Weapon
- Finding Your First Bug: Realistic Targets
- Writing a Good Report
- Top Bug Bounty Platforms to Join
- Success Stories from Bug Bounty Hunters
- Final Thoughts: Your Bug Hunting Journey Starts Now
What Is Bug Bounty Hunting?
Bug bounty hunting is the practice of identifying and responsibly disclosing security vulnerabilities in software, systems, or websites in exchange for rewards, often monetary. These programs are run by companies or third-party platforms that encourage hackers to find bugs ethically and report them, rather than exploit them.
Think of it like being a digital locksmith—helping companies identify where the “doors and windows” are left open, so they can fix them before the burglars come.

Why Become a Bug Bounty Hunter?
There are multiple reasons why ethical hackers dive into bug bounty hunting:
- Earning Potential: Top hunters can make six figures or more annually.
- Skill Development: Learn and apply real-world penetration testing skills.
- Global Community: Collaborate with researchers from around the world.
- Flexible Schedule: Work anytime, from anywhere.
- Recognition: Get listed in “Hall of Fame” pages, CVEs, or bounty leaderboards.
What Skills Do You Need to Start?
You don’t need a degree to start bug bounty hunting, but a solid grasp of technical fundamentals is necessary. Here’s a breakdown of key skills:
Networking & HTTP Protocols
Understanding how the internet works is foundational. Learn how requests, responses, cookies, sessions, and headers work.
- Tools: Wireshark, Burp Suite, Postman
- Learn: OSI Model, TCP/IP, DNS, HTTP/HTTPS
Web Technologies
Know the basics of how web applications are built and run.
- HTML, CSS, JavaScript
- Databases: MySQL, MongoDB
- Backend: PHP, Node.js, Python
Security Concepts
Start with the OWASP Top 10 vulnerabilities:
- QL Injection
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- Broken Authentication
- Insecure Direct Object References (IDOR)
Hands-On Practice
Theory alone won’t help. Practice in safe, legal environments like:
- DVWA (Damn Vulnerable Web App) For more details visit: DVWA
- WebGoat
- Hack The Box
- PortSwigger Labs
Setting Up Your Home Lab
Before jumping into live targets, practice in a controlled environment. Here’s how:
Install Virtual Machines
- Use tools like VMware or VirtualBox and install Kali Linux and vulnerable apps like DVWA, Juice Shop, or bWAPP.
Use Burp Suite
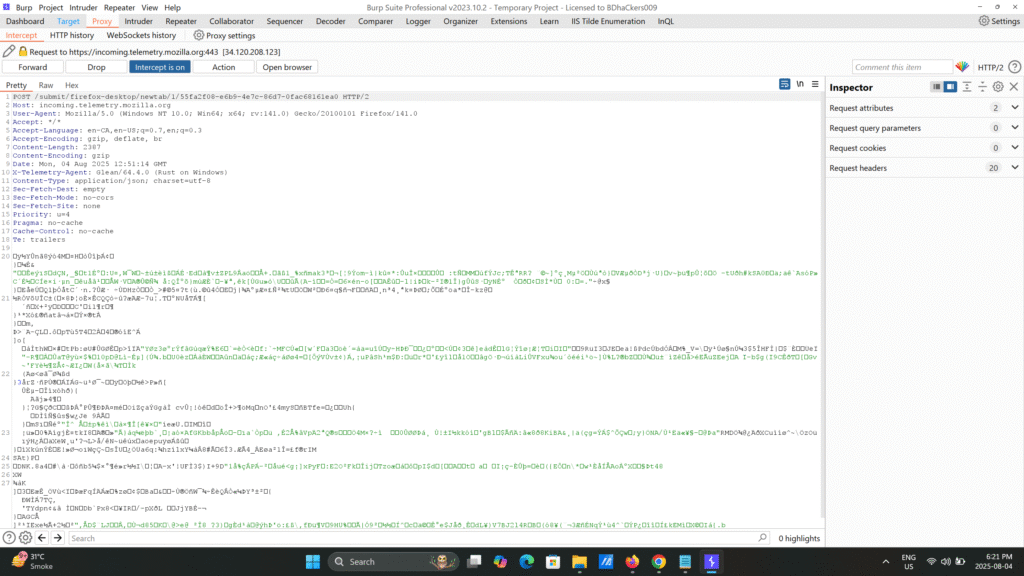
- This is your go-to toolkit for intercepting and modifying web traffic. The Community Edition is free and very powerful for beginners.
Note-Taking Tools
- Keep track of bugs, payloads, recon data, and tips. Tools like CherryTree, Obsidian, or even Notion help with organized tracking.
Tools of the Trade
Here are essential tools bug bounty hunters use regularly:
| Tool | Purpose |
|---|---|
| Burp Suite | Intercepting and modifying web requests |
| Nmap | Network scanning |
| Amass/Subfinder | Subdomain enumeration |
| SQLmap | Automated SQL injection tool |
| Wayback Machine | Finding archived endpoints |
| FFUF/Dirsearch | Directory fuzzing |
| httpx | Web server probing |
| Shodan/Censys | Finding exposed devices |
Reconnaissance: Your First Weapon
Recon is the art of collecting as much information about a target as possible—like subdomains, open ports, technologies used, endpoints, and more. Good recon leads to good bugs.
Use tools like:
- Amass or Subfinder for subdomain discovery.
- httpx or nmap to probe live hosts.
- Waybackurls or gau to find hidden/old endpoints.
Finding Your First Bug: Realistic Targets
Once you’ve built confidence in your skills, try your hand at real-world bug bounty programs. Start small—go for low-hanging fruit like:
- Open Redirects
- Missing Security Headers
- Broken Access Controls (like viewing someone else’s data)
- IDORs in APIs
Don’t chase only high-severity bugs. Focus on valid ones.
Writing a Good Report
Finding a bug is only half the job. You must communicate it clearly:
A great bug report includes:
- Title: Clearly state the vulnerability.
- Summary: What is the bug, and how does it impact the system?
- Steps to Reproduce: Include clear steps, with screenshots or videos.
- Impact: Explain why it matters.
- Recommendations: Suggest a fix, if possible.
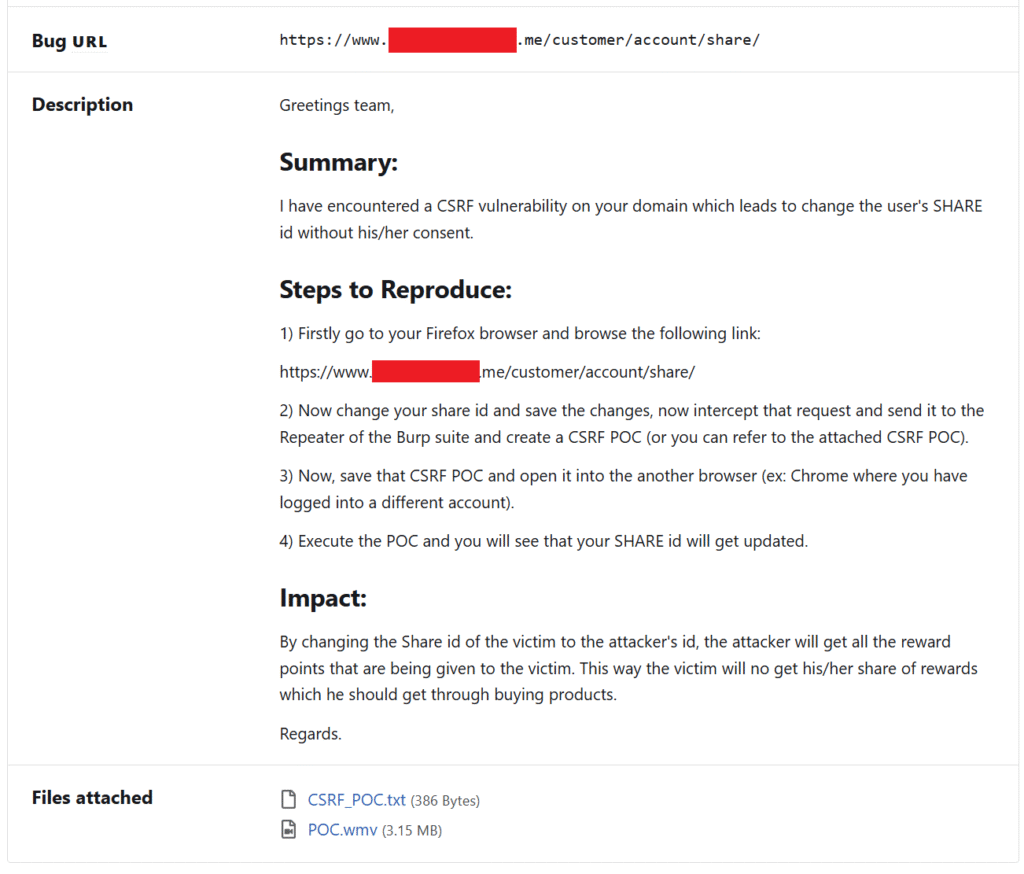
Pro Tip: Even a $10 bug can earn you $100 if your report is clean, reproducible, and helpful.
Top Bug Bounty Platforms to Join
Here are the major platforms where companies list their programs:
HackerOne
- Big clients: Uber, Twitter, Shopify, PayPal
- Pros: Beginner-friendly, good triage team
- Website: https://hackerone.com
Bugcrowd
- Clients: Atlassian, Mastercard
- Good triage, private programs
- Website: https://bugcrowd.com
Synack Red Team (SRT)
- Invite-only, but high payouts
- Focuses on elite researchers
- Website: https://www.synack.com
Intigriti
- Based in Europe, great for EU residents
- Features public and private programs
- Website: https://www.intigriti.com
YesWeHack
- European-focused, GDPR-compliant programs
- Website: https://www.yeswehack.com
Open Bug Bounty
- No registration needed
- Good for beginner practice (public disclosures)
- Website: https://www.openbugbounty.org
Success Stories from Bug Bounty Hunters
Many top bug bounty hunters today started with no formal education in cybersecurity. Some examples:
- @ngalog earned over $100K on HackerOne by finding web misconfigurations.
- @try_to_hack became a full-time bounty hunter, working from anywhere.
- @zseano runs paid training courses and offers mentorship to new hackers.
The path is open. With effort, consistency, and curiosity—you can get there too.
Final Thoughts: Your Bug Hunting Journey Starts Now
Bug bounty hunting isn’t just about making money—it’s about learning, growing, and giving back to the security community. You sharpen your technical skills, help secure digital assets, and build a reputation in a high-demand field.
There are no shortcuts to success here. But if you’re committed, curious, and ethical—you’ll not only get paid but also become part of a passionate, global movement of security researchers shaping the internet’s safety.
📚 Enjoyed this post?
Check out some of our other trending blog posts and stay ahead in the world of tech, AI, and cybersecurity.
🔎 Explore More Posts